Download our free SNMP White Paper. Featuring SNMP Expert Marshall DenHartog.
This guidebook has been created to give you the information you need to successfully implement SNMP-based alarm monitoring in your network.
1-800-693-0351
Have a specific question? Ask our team of expert engineers and get a specific answer!
Sign up for the next DPS Factory Training!

Whether you're new to our equipment or you've used it for years, DPS factory training is the best way to get more from your monitoring.
Reserve Your Seat TodayYou're responsible for keeping your network online and secure. That includes preventing unauthorized access and tampering. You may even be required by management or the government to comply with certain security standards.
You probably have older equipment that doesn't support SNMP. You might have new security standards that require SNMPv3 and don't allow unencrypted SNMP v1/v2c.
For these situations, you need a device to bridge the gap between new and old equipment, as well as new and old standards. When your equipment spans multiple generations of technology (this is true at 99% of companies), you need conversion/mediation devices to bridge the gap. Throwing out your entire system and building a new one every time technology evolves just isn't feasible.
The Simple Network Management Protocol (SNMP) is based on the manager/agent model, and it has three major versions: SNMPv1, SNMPv2c, and SNMPv3.
SNMPv1 was the first version of SNMP. Although it accomplished its goal of being an open, standard protocol, it was found to be lacking in key areas for certain applications. Later versions have addressed many of these problems. Smaller RTUs commonly support SNMPv1.
SNMPv2c is a sub-version of SNMPv2. Its key advantage over previous versions is the Inform command. Unlike Traps, which are simply received by a manager, Informs are positively acknowledged with a response message. If a manager does not reply to an Inform, the SNMP agent will resend the Inform.
Other advantages include:
To delve deeper, the SNMP Inform request is a new type of SNMP communication introduced specifically in SNMPv2c. This feature is primarily used for manager-to-manager communication. The Inform request serves a crucial role: it acknowledges the receipt of notifications.
One of the standout characteristics of the SNMP Inform request is its reliability. The packet will be sent continually until the sending SNMP manager receives an acknowledgment. This ensures that alerts are not missed and facilitates better communication between network managers, enhancing the overall efficiency and dependability of network management.
Keep in mind that not all network devices are SNMPv2c compliant, so your SNMP manager should be downward compatible with SNMPv1 monitored devices. You can also use an SNMPv3 mediation device to ensure compatibility.
SNMPv3 is the newest version of SNMP. Its primary feature is a higher level of security.
The "EngineID" Identifier in SNMPv3 uniquely identifies each SNMP entity. Conflicts can occur if two SNMP entities have duplicate EngineID's. The EngineID is used to generate the key for authenticated messages.
SNMPv3 security comes primarily in 2 forms:
Authentication
Authentication is used to ensure that traps are read by only the intended recipient. As messages are created, they are given a special key that is based on the EngineID of the entity. The key is shared with the intended recipient and used to receive the message.
Privacy
Privacy encrypts the payload of the SNMP message to ensure that it cannot be read by unauthorized users. Any intercepted traps will be filled with garbled characters and will be unreadable. Privacy is especially useful in applications where SNMP messages must be routed over the Internet.
By integrating these improved features, SNMPv3 provides a robust framework for secure and efficient network management, making it ideal for environments where security and data integrity are paramount.
These different generations of the SNMP protocol have created a definite fracturing of what was once a simple architecture. Now, you have to consider the multi-generational SNMP versions you have in play and consider mediation devices to convert older SNMP to the newer version.
If your network has evolved over time (as every network has), you have a problem: Many of your SNMP-based devices don't support SNMPv3 authenticating and encrypting your data.
Because encryption is an intensive operation for small hardware, firmware updates won't save you. And you can't simply replace all of your SNMP-based equipment all at once. No one has the budget to simultaneously upgrade equipment that was installed over a 20-year period.
How much SNMP v1 & v2c equipment do you have in your network? At most companies, it's a big number.
You're going to need some amount of new hardware to upgrade to SNMPv3, but you need to be surgical. You can't afford to replace all of your equipment.
Despite the obvious advantages of an open standard, early versions of SNMP (v1 & v2c) were not built with security in mind. This poses a big challenge today if you work at a security-conscious organization, like a utility or government entity, that now requires encrypted SNMPv3.
If you've got a lot of SNMP v1 & v2c equipment in your network combined with a requirement to use only secure SNMPv3, it may seem like you've been given 2 incompatible goals:
Stop using all of your SNMP v1 & v2c equipment.
Don't spend budget money on new SNMPv3 equipment.
What you need is a small number of converter devices that take in SNMPv1/v2c traps from many sources and convert those traps to SNMPv3.
Accepts inbound SNMPv1/v2c traps from many different source devices (much less purchasing than a complete system swap-out)
Sends SNMP v3 traps to your SNMP manager (messages are secured before forwarding)
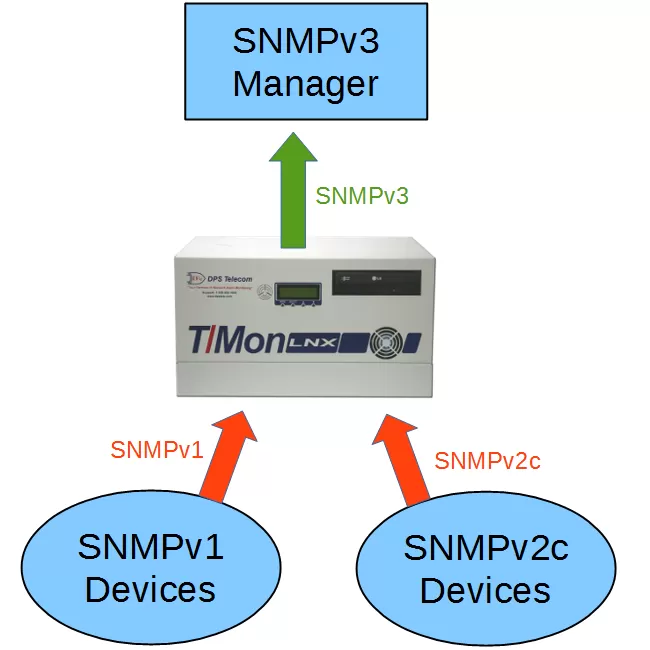
One way to meet the two requirements above is to install an intelligent alarm master station that accepts inbound SNMPv1/v2c and translates those traps to SNMPv3. This means you only have to buy one device, install one device, and configure one device. Unless you have a very small network, this is going to be the simplest, cheapest way for you to upgrade to SNMPv3.
There are some limitations to using a single master station:
You have a single point of failure. (You can choose to install a redundant pair of masters to address this)
You'll still be using unencrypted SNMP until traps reach the central master (Your overall network architecture should be a big factor in your decision. Do you have other security in place to compensate for the SNMPv1/v2c segments?)
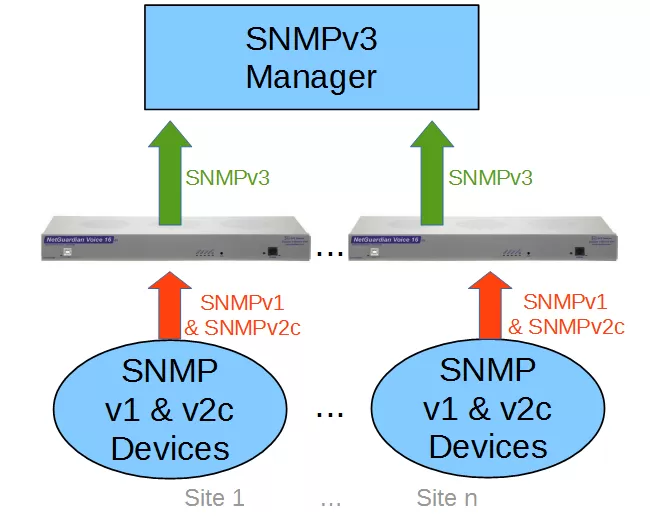
The alternative to a central master station is a decentralized fleet of SNMPv3 converters. These are small devices (typically 1 RU) that can handle a reasonable number of inbound SNMP traps. Because you'll be deploying more than one converter, each one needs to handle just a fraction of your total SNMP traffic.
Your older SNMP equipment will send unencrypted traps only as far as the local NetGuardian (not across the wider network). The NetGuardian will convert the trap to SNMPv3 and send it back to your central SNMP manager. You'll comply with your security rules without blowing your budget on brand-new infrastructure.
This decentralized architecture addresses several of the potential problems of a single master station:
You'll eliminate the single point of failure. (The loss of a single converter device will have no effect on any other)
No unencrypted SNMP leaves the site/area. (With a device in each building/zone, you won't have unencrypted SNMP traffic traveling across any significant part of your network)
Remote converters can handle other functions. (You can generally address other monitoring/control tasks using "freebie" included functions on the converter device).
If you can handle the possible one-time increase in purchasing and select Option B - which is still minuscule compared to a total upgrade of all of your SNMP-based gear - you'll gain several advantages over Option A.
It's worth comparing Option A and Option B for yourself and your network. Remember, though, that doing nothing might be the most expensive choice of all. Business momentum ebbs and flows. You might be focused on SNMP today, but you're liable to get pulled onto a totally different project tomorrow.
While you're able to focus on SNMP conversion, get a few quotes together. That's what it takes to get funding (or at least get something into your next budget).
At DPS, we receive many quote requests after "Do Nothing" comes back to bite you. You have no reason not to be proactive (and maybe you'll manage to impress your boss).
Call us. Chat with an expert for 10 minutes. We'll email you a detailed quote with a custom application drawing. We'll even include a summary of business benefits you can use to justify your project budget.
Call 1-800-693-0351 now for your quote (or send us a quick online message instead)