Download our free SNMP White Paper. Featuring SNMP Expert Marshall DenHartog.
This guidebook has been created to give you the information you need to successfully implement SNMP-based alarm monitoring in your network.
1-800-693-0351
Have a specific question? Ask our team of expert engineers and get a specific answer!
Sign up for the next DPS Factory Training!

Whether you're new to our equipment or you've used it for years, DPS factory training is the best way to get more from your monitoring.
Reserve Your Seat TodaySecuring your alarms and controls from unauthorized users can be difficult. Even so, you can't afford to leave your network vulnerable. You know exactly how much downtime costs you.
The NetGuardian 832A G5 is a large-capacity RTU that monitors 32 discrete alarms and 8 analog alarms, pings 32 network elements, and controls 8 relays. It also provides LAN reach through access to 8 serial ports, and reports via SNMP or DCPX, e-mail, or pagers.
The NetGuardian G5 boasts several enhancements from previous NetGuardian models. These include advanced hardware, increased processing speed, and enhanced security options.
As a matter of fact, the NetGuardian G5 platform has a lot of power to provide you with advanced security measures. Although there are many different build options, each of them includes SNMPv3 encryption and RADIUS authentication as standard features.
There have been several versions of the Simple Network Management Protocol (SNMP). These different generations of SNMP have created a definite fracturing of what was once a simple architecture. Now, you have to consider the multi-generational SNMP versions you have in play and consider mediation devices to convert older SNMP to the newer version.
The latest (SNMPv3) adds encryption for the secure transmission of critical data. This presents a problem if you have a large deployment of earlier gear that only uses SNMPv1 or SNMPv2 (v2c is the most common sub-version of v2).
It's important to determine which is best for your unique monitoring applications. If you need the most secure data transmission available, you should monitor strictly in SNMP v3 protocol. However, if you're in an environment where high-level security is not necessary, it's probably better to stick with SNMP v1 or v2c if that's what you already have.
SNMPv3 security comes primarily in 2 forms:
Authentication
Authentication is used to ensure that SNMP trap messages are read by only the intended recipient. As messages are created, they are given a special key that is based on the EngineID of the entity. The key is shared with the intended recipient and used to receive the message.
Privacy
Privacy encrypts the payload of the SNMP message to ensure that it cannot be read by unauthorized users. Any intercepted traps will be filled with garbled characters and will be unreadable. Privacy is especially useful in applications where SNMP messages must be routed over the Internet.
Furthermore, most organizations that care about security would prefer to also encrypt SNMP protocol in order to have redundant security layers.
If you're transitioning to SNMPv3 in your network, the NetGuardian 832A G5 can help you make the change.
The NetGuardian G5 can report alarms in three versions of the SNMP protocol: v1, v2c, or v3. This allows you to report alarms, no matter what SNMP version you are using. You can start reporting alarms in SNMP v1 or v2c and switch over to v3 whenever you're ready.
You have the ability to choose which SNMP versions are permitted to talk with your NetGuardian. By allowing v3 access only, you require all users and SNMP managers to use the v3's enhanced security. In cases where security is less of a concern, you can choose to allow all SNMP versions.
SNMPv3 is the most secure version of SNMP, and the NetGuardian 832A G5 platform encrypts its messages with CBC-DES encryption, a part of the Universal Security Model (USM).
The NetGuardian 832A G5's ability to provide security is enhanced by its support of up to four v3 user profiles. Each user is assigned a unique set of security parameters, including authentication and/or privileged access. Authentication can be based on the MD5 or SHA algorithm. With either option, messages may be encrypted using DES 56-bit encryption based on the CBC-DES standard, allowing for max security and flexibility.
The encrypted data appears scrambled if it is hacked, rendering it unreadable by anyone but the intended recipient. This form of encryption makes SNMPv3 your best form of protection when routing SNMP messages over the Internet. This is key for companies that require high levels of security, authorization, and access control.
Communications between the NOC and remote access points are a vital piece of the puzzle in a network monitoring system. Without the ability for a technician to access the database of alarms and activities, or for the administrator to edit permissions and usage restrictions, you may as well be attempting to fly blind. While, allowing wide open access from across the network is out of the question, many people have tried to implement various security measures to verify the user attempting to gain access. One of these methods is through the utilization of RADIUS.
Remote Authentication Dial-In User Service protocol developed by Livingston Enterprises, Inc., is used as an access server authentication and accounting protocol. Using the client/server format, RADIUS passes user information to designated servers and acts on the response that is returned.
The tasks of the server include receiving client requests to connect, authentication of the user, and the return of configuration information necessary for the client to deliver services to the user. While serving as a proxy client, a RADIUS server can allow the client to connect to other RADIUS servers or other kinds of authentication methods. It can support PPP, PAP, or CHAP, UNIX login, as well as several other methods.
A user login consists of several steps:
Query (Access-Request)
Response (Access-Accept/Reject/Challenge and corresponding parameters)
Reply (client acts upon information received by server)
Another built-in feature of RADIUS authentication methods is the ability to account for all attempts at access, authorization, and user activities while utilizing one of the many client devices.
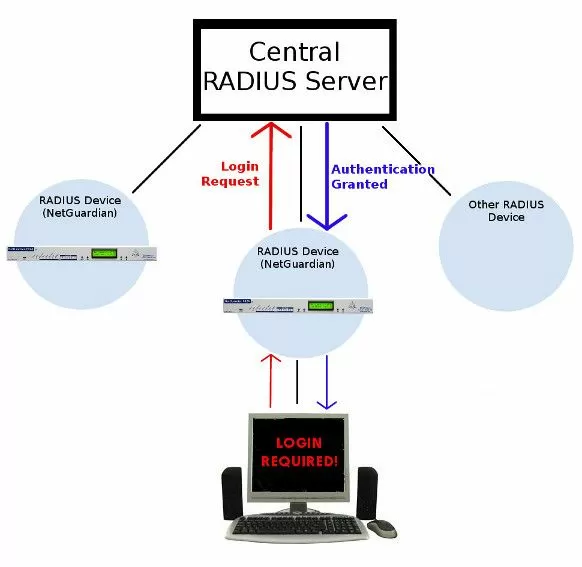
RADIUS (Remote Authentication Dial In User Service) provides a way to manage logins to many different types of gear in one central location. The basic architecture is very simple: many RADIUS devices connect to a central RADIUS server. Every time a network device receives a login attempt (usually a username & password), it requests an authentication from the central RADIUS server.
All authentication requests are handled by the central server and not the managed devices themselves. Therefore, updating user profiles and access permissions only has to be done in one place.
Key Advantages of RADIUS on the NetGuardian G5 platform.Virtually unlimited users
With RADIUS, the number of user logins you can support is huge. Most likely you will never run out.
Centralized management
You'll also be able to manage your logins from your central RADIUS server. You'll never have to worry about updating any single remote. If an employee leaves your company, you can revoke their access rights very easily.
Integration with enterprise management
When your alarm remotes use the same RADIUS authentication method as your other important gear, you reduce the complexity of managing your gear. It's always easier to manage a single umbrella than it is to keep track of several unrelated systems.
The importance of using the best can't be understated. Using a high-quality RTU gives you the peace of mind of knowing that your network is fully protected. That's why it's important to choose the best technology for your scenario.
The NetGuardian 832 g5 is just one example of a secure RTU from our line of remotes that could be a perfect fit for your scenario.
Independently of which RTU is the best for your unique scenario, all of our products are supported by two-year hardware warranties, technical support, free lifetime firmware upgrades, and a risk-free, money-back guarantee.
If you're also looking for a secure master station, our T/Mon also has the option to support HTTPs web viewing, and - like the NetGuardian line - it has passwords that control the level of access individual users have to the system.
There's a lot to consider when it comes to choosing the right network monitoring hardware. So, call or email us and we can help you figure out the right fit device for you.