Download our free Monitoring Fundamentals Tutorial.
An introduction to Monitoring Fundamentals strictly from the perspective of telecom network alarm management.
1-800-693-0351
Have a specific question? Ask our team of expert engineers and get a specific answer!
Sign up for the next DPS Factory Training!

Whether you're new to our equipment or you've used it for years, DPS factory training is the best way to get more from your monitoring.
Reserve Your Seat TodayViruses are an everyday concern for anyone using a computer. Any network equipment you have deployed that supports a web interface is vulnerable to malicious virus attacks. Including your network monitoring gear.
Your monitoring telecom tools are tasked with an important job: monitor your critical network equipment to ensure optimum reliability. If your remote monitoring and control equipment is compromised by a malicious virus or malware attack, your wider network will be vulnerable. You can't afford to let a security hole with your monitoring gear expose your entire network.
On top of having a more reliable network monitor, you'll also comply with many security standards. Many organizations are faced with standards and regulations that must be met (for example, NERC regulations). So, deploying security-enhanced monitoring gear can help you attain that compliance.
Accessing your monitoring devices via a web interface on consumer-grade hardware will always be risky. Malicious viruses can sneak into your telemetry system and expose your sensitive network data.
These kinds of virus attacks create two problems. First, a virus always comes with a repair bill. You're going to have to spend time and resources fixing any computer that's infected. This wastes manpower and resource costs.
Secondly, any downtime caused by a virus attack can easily upset your customers - causing them to take their business elsewhere. These two issues are easily avoided when using security-enhanced features for your network monitoring gear.
Which security features make DPS Telecom monitoring equipment so secure?
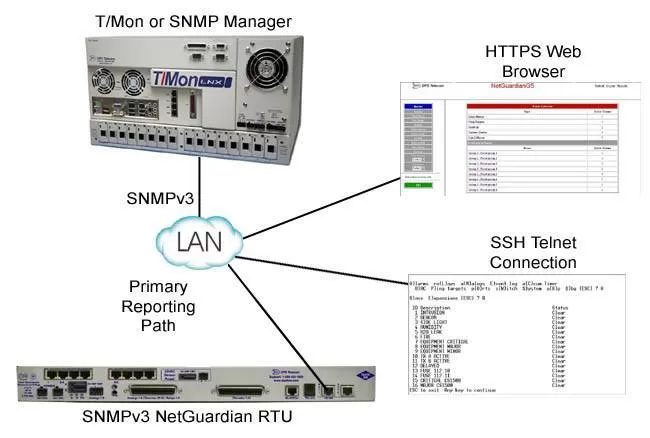
See the NetGuardian 420, NetGuardian 216F, and NetGuardian 832A / 864A for examples of devices with SNMP v3 support.
SSH Support
Connect securely via Telnet/serial connection with SSH support. If you're going to be accessing your gear via text-based interfaces, then you'll want optimum security. With DPS equipment, you can select build options with SSH - so your Telnet connections will always be secure.
RADIUS Authentication
This capability gives you superior control over user access to your equipment. With RADIUS authentication, your RTUs, master stations, and other equipment can now pass authentication attempts to a central server. You can limit access rights from this centralized user database to restrict/allow specific privileges. See the NetGuardian 832A G5 for a product that uses secure RADIUS authentication.

Having control over your user access and permissions can protect you from an unauthorized user from causing damage. All DPS gear supports user-level permissions - giving you complete control over the privileges you grant to your users.
Multiple Network Interfaces (NICs)
With several network interface cards (NICs), you can support your networks. While not having to worry that your monitoring gear can be accessed by an unauthorized network intruder. The equipment is on multiple networks, but does not route traffic between them. The NetGuardian 832A supports dual NICs and the T/Mon LNX supports 6 NICs - giving you lots of visibility.
Know that these products have been tested with multiple industry-standard vulnerability assessment tools and that they all passed.
There's a lot you can do to protect your network monitoring. Your sensitive and important alarm data should never be vulnerable to malware and outside attacks. Simple precautions and the right vendor can provide you with secure equipment to truly protect your network in real-time.
If you're ready to protect against viruses and malware and get peace of mind, contact the DPS Telecom secure monitoring experts. Even if your security need is unique, DPS will work to create a specific solution just for you.
For one security-conscious client, DPS created a one-way protocol and removed control relays from the device. This allowed their remote sites to report information to their master, without their master being able to control or access their sites. This prevented any hacker from gaining control over the equipment in their network.
To get started tackling your secure alarm system challenges: