Check out our White Paper Series!
A complete library of helpful advice and survival guides for every aspect of system monitoring and control.
1-800-693-0351
Have a specific question? Ask our team of expert engineers and get a specific answer!
Sign up for the next DPS Factory Training!

Whether you're new to our equipment or you've used it for years, DPS factory training is the best way to get more from your monitoring.
Reserve Your Seat TodayIf you want to reduce your windshield time, the NetGuardian 832A's built-in terminal server is a great tool. The NetGuardian gives you convenient LAN - or dial-up - access for controlling, configuring, and rebooting equipment like PBXs, switches, routers, or other serial equipment.
The NetGuardian terminal server is easier and more cost-effective than any of the alternatives: unnecessarily sending technicians to operate remote site equipment; installing expensive dedicated circuits; or buying a separate terminal server and RTU.
Easy access to your revenue-generating equipment is great, but how do you restrict that access to authorized personnel? You can protect your equipment with the NetGuardian's security password - for users without the right password, the ports to your equipment don't even exist.
The NetGuardian supports two kinds of proxy connections, direct and indirect. Indirect connections are more secure than direct connections.
Indirect connections are inherently secure, because they are mediated by the NetGuardian interface, and the entire NetGuardian interface is protected by passwords. Users need a password to gain access to any NetGuardian function, and the unit administrator can define and limit the access privileges of each individual user.
Direct connections are not password protected. A direct connection is a ordinary, unmediated Telnet link between your computer and a TCP port, bypassing the NetGuardian interface and its password security. A direct connection can be invoked straight from the command line by entering the telnet command, the IP address of the NetGuardian, and the number of the target TCP port.
You can ensure the best possible security for your proxy connections by disabling direct proxy connections.
There's a quick-and-dirty way to disable direct proxy connections: set the TCP port to an uncommon value. But that's only security by obscurity. The TCP port is still available for a direct connection, if anyone can find it.
The right way to secure your NetGuardian's proxy port is by using the NetGuardian's port definition interface to disable all TCP access.
To do this, your NetGuardian must have firmware version 2.6H or later. Download the latest version of the NetGuardian firmware.
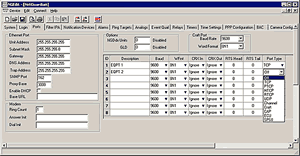
Here's how it's done: Connect to the NetGuardian using either NGEdit, the Web Browser Interface, or the TTY interface, and navigate to Port Definition, as shown in the side figure. (The example shown is from NGEdit, but any of the NetGuardian's software configuration interfaces will do).
To disable TCP access, simply set the Port Type to Off, as shown. When set to Off, the port is no longer associated with a TCP socket, completely disabling the port from direct proxy connection.
In the screenshot, Port 1 is configured as a TCP port to connect to a device labeled EQPT 1. This device can be reached by both direct and indirect connections. Port 2 is associated with a device labeled EQPT 2, but its Port Type is set to Off.
EQPT 2 can't be accessed by a direct proxy connection, but it's still available through an indirect proxy connection, mediated by the NetGuardian and its password protection. Authorized users with the correct password can log on to the device. Users without the correct password are shut out.
This is just one of the ways the NetGuardian helps you securely manage your remote sites and your remote site equipment. You can find out about everything the NetGuardian can do for you on our NetGuardian page. Check it out!