Check out our White Paper Series!
A complete library of helpful advice and survival guides for every aspect of system monitoring and control.
1-800-693-0351
Have a specific question? Ask our team of expert engineers and get a specific answer!
Sign up for the next DPS Factory Training!

Whether you're new to our equipment or you've used it for years, DPS factory training is the best way to get more from your monitoring.
Reserve Your Seat TodayMany companies are facing serious challenges due to the measures being taken to contain the Coronavirus pandemic. With the stay-at-home order, many employers are being forced to operate and manage their networks completely from home.
If you have a remote gear and processes that are vital for your operations, you need to be able to ensure that your technicians can adapt to the "new normal" and are equipped to do their jobs of monitoring alarms away from their offices.
You might already have a remote monitoring system in place, but now you need to prepare your team to efficiently manage it from their homes. Let's take a look at how your employees can efficiently monitor network alarms from wherever they are.
Downtime, now more than ever, brings a huge financial impact to companies that have networks at remote locations. A competent monitoring system will allow you to keep track of your remote equipment and keep track of your processes.
Having full visibility of your alarm data can help you maintain your mission-critical network running smoothly and at full capacity even during hard times in our society. Of course, priorities are not the same right now, but keeping your business running as close to normal as possible is critical for your employees and clients.
Staying at home is important to maintain the health of your team, but it may not be possible for them to create the exact same space that they have at work. However, an efficient remote monitoring system will have important features that will allow them to keep working productively even from home.
Some of these main features are:
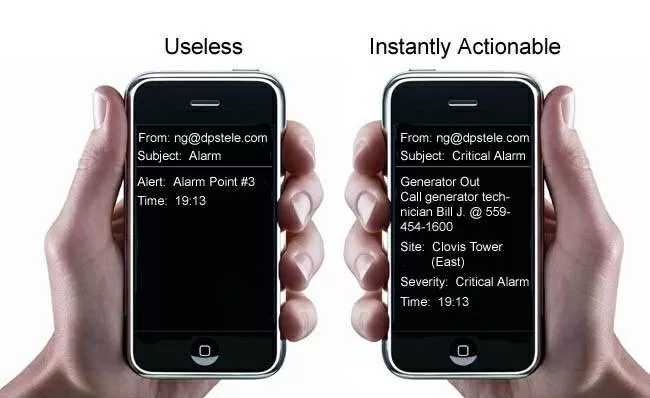
Receiving alerts from your monitoring system is your first line of defense. You need detailed and actionable information in order to correct a problem. Unclear and incoherent alerts won't help you prevent not react to network issues.
Your techs should be receiving alerts with sufficient details so they are able to adequately respond. But, they also need to know if the alarm was cleared. This is especially important if they are on their way to a remote site because they can't simply go back and avoid spending time and resources for a condition that doesn't represent an alarm anymore.
Also, the notifications need to reach you wherever you are. Especially if your team is working from home, they need alternatives ways to receive alerts, such as text messages and phone calls. Moreover, if the first person notified isn't able to react to an alarm within a time frame for whatever reason, another tech should be notified and so on - until someone acknowledges it.
Effective alerts will make your team can stay on top of any issue occurring at your remote sites even if they are not working at the office.
Being able to remotely monitor your equipment and processes is essential to maintain operational uptime even during a quarantine. But, being able to remotely take action when an issue is detected is critical.
An efficient remote monitoring and control system will provide control relays and serial data ports on top of discrete and analog inputs (which are used to gather monitoring data). Control relays can be used to operate any device that's normally operated by a button or switch.
A control relay is simple contact closure that will either latch or release depending on the command it receives. You can configure your relays to latch when you want, allowing you to remotely open doors, turn on generators, etc.
Now, it's great to be able to remotely operate your equipment, but since your team will be working from home they can be easily distracted and miss an alarm and not manually operate a relay. So, the best systems allow you to pre-program rules for each control relay you have. Whenever these conditions are met, your RTU will automatically latch a control relay.
Your tech will still get a notification but your RTU will correct the situation even if he's not paying attention.
Now, more than ever, it's important to have your team focused on real alarms.
If your alarm management system is always sending out notifications about events that don't require any action, your technicians will become more and more desensitized to alerts. This will defeat the purpose of having a monitoring system in the first place because your techs might stop taking all alarms into consideration.
These non-essential, recurring notifications are called nuisance alarms. Make sure your monitoring system has the capability of filtering them, so your team can remain productive and can prevent problems from becoming real network threats.
Working from home can already be really distracting. So, make sure your team can remain efficient and focus their efforts on real issues by filtering nuisance alarms.
This functionality of filtering nuisance alarms will include the following features:
With employees continuing to work from home, it's a priority for most organizations to ensure that their teams can carry out their tasks securely.
Security concerns was already a big factor for many companies, but now it is even more critical because it involves accessing mission-critical networks from computers at home. It's essential to be able to protect your network against data breaches, hacks, cyberattacks, ransomware threats, and phishing scams.
It's important to remember, though, that even when your staff is not on the clock, your network might still be at risk. So, make sure your remote monitoring system has the latest features and capabilities to ensure the safety of your network information.
Some of these features are:
Since your employees will probably be accessing the monitoring system from ordinary computers and web browsers, your system might be susceptible to viruses and other security holes. In order to protect your mission-critical data and equipment, your monitoring system needs to be secured from open internet access.
Your network master station interface should support secure web access over HTTPS. The HTTPS module supports Hypertext Transfer Protocol over Secure Socket Layer, which is the industry-standard secure web protocol for online sales and financial transactions.
So, when you access your master station's interface using HTTPS, the server establishes a secure connection to your web browser. The data traveling through a secure connection will be encrypted. This way, the information will be protected against eavesdropping and "man in the middle" attacks.
Remote Authentication Dial-In User Service (RADIUS) technology is an industry best practice for an authentication method. It gives you a way to administer logins to your many different types of devices in one central location.
The RADIUS structure is fairly simple. Multiple RADIUS equipment is connected to a central RADIUS server. This means that every time a device receives a login request (usually through a username and password combination), it will request authentication from the central RADIUS server.
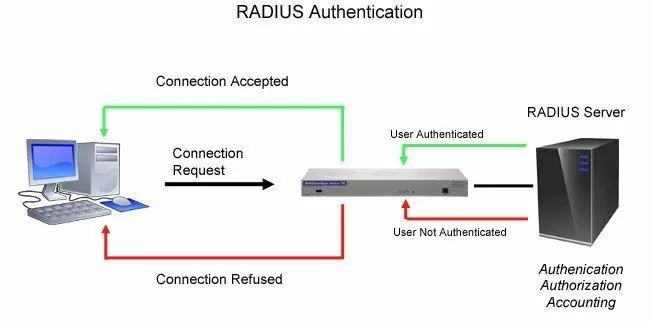
All the authentication requests are controlled by the central server and not the devices themselves. So, updating user-profiles and access permissions can only be done in one main place. The RADIUS capability gives your network many security advantages, such as:
The Simple Network Management Protocol (SNMP) is a common communication protocol in many remote monitoring systems. The latest version of SNMP, the SNMPv3, comes with encryption to provide secure transmission of data.
SNMPv3 security comes in 2 main forms:
NetGuardian RTUs and the T/Mon Master Station follow these and many other security best practices.
Today, social distancing has changed our daily lives and it's safe to say that viruses can spread easily in environments like workplaces. For many companies who are now operating with minimal staffing or fully remote teams, this also means changes to who has building access and how employees are coming and going.
Most companies with the network at remote sites, never had employees working regular shifts at these locations, they simply send teams to fix issues when needed. Even so, there are still security risks that need to be taken into consideration:
One way to minimize and even eliminate these problems is by deploying a modern building access system. The DPS Building Access System is a complete electronic access control platform that prioritizes the protection of the user and facility. It has many features and functionalities that not only protect your mission-critical network but also prevents the spread of germs.
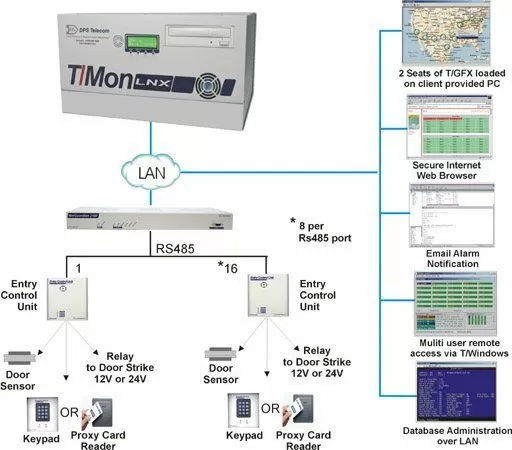
The DPS Building Access System offers multiple tools to provide an efficient remote security management system. Here are some of them:
We can provide you with a custom access control solution that will give you the flexibility to tailor your system to suit your unique requirements.
Many companies in the US have their employees working from home in order to help prevent the spread of COVID-19. Some of these organizations were hesitant to deploy remote monitoring systems before (many of them thought of monitoring systems just as a cost center), but now they found that they can actually bring many benefits.
Remote monitoring systems have the capacity to offer a safe way for staff to keep managing remote equipment and processes and to successfully maintain network uptime.
Effectively deploying a monitoring system for the first time and being able to successfully work with it is a big task. So, having a system with competent features is essential for your success.
Counting on an experienced remote monitoring solutions vendor to provide you with an efficient system is critical. Your provider should be able to help you get a perfect system for what you need. As a vertically integrated manufacturer we know how important it is to only give you a perfect-fit solution, but also to support you in many ways.
A new remote monitoring system can feel overwhelming, but we can help you. We will design a system that will meet all your requirements, we will manufacture it in house and we also offer tech support and training. We can prepare you and your team to effectively manage your remote network and get through these hard times. We are just a call away.

Morgana Siggins
Morgana Siggins is a marketing writer, content creator, and documentation specialist at DPS Telecom. She has created over 200 blog articles and videos sharing her years of experience in the remote monitoring industry.