Check out our White Paper Series!
A complete library of helpful advice and survival guides for every aspect of system monitoring and control.
1-800-693-0351
Have a specific question? Ask our team of expert engineers and get a specific answer!
Sign up for the next DPS Factory Training!

Whether you're new to our equipment or you've used it for years, DPS factory training is the best way to get more from your monitoring.
Reserve Your Seat TodayYour remote sites are vulnerable. This is especially true if you have an isolated and unmanned site with unsupervised workers coming and going all the time and propping open doors - because they might end up forgetting to close them.
This turns your remote sites into an easy prey for thieves and vandals (animals and bad weather are not excluded either).
Unfortunately, the traditional ways to control remote access, such as a lock-and-key system, are neither practical nor cheap.
Keys can be lost, stolen, or copied and are difficult to keep track of.
Let's take a look at how you can effectively manage site access and prevent risks from propped doors open without blowing a hole in your budget.
A Building Access System (BAS) is easy to install and a comprehensive building management system that integrates into an existing alarm management platform. With the system in place, a log of all site access, including the time of day and location that access was granted, is maintained. In addition, alarms such as intrusions and excessive access attempts are reported to T/Mon on a per-door basis.
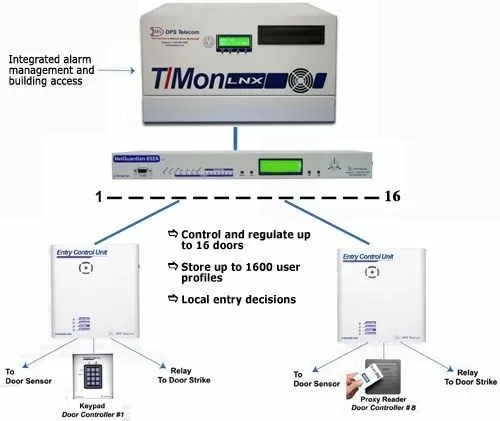
The BAS system provides valuable security to your remote sites and deters theft, break-ins and vandalism. And the system consists of:
A master station
An RTU
An Entry Control Unit
And a Proxy Reader
The BAS works as a software module in the T/Mon software. It assigns each user with a unique user profile containing information such as which sites are allowed to be accessed, the door numbers, days of the week access is allowed, a start/stop time, and a beginning and ending date (primarily for contractors, new employees, or short term employees).

There is also theT/Mon BAS. T/Mon BAS gives you centralized, electronic control over your doors.
You can use T/Mon BAS to:
Grant individual door access rights for up to 1,300 users
View and control access from all of your facilities on one screen
Monitor unauthorized door access attempts and intrusion alarms
Remotely "buzz-in" site visitors from your central office
Maintain access history logs for review after an incident

T/Mon BAS gives you the advanced access control capabilities of T/Mon LNX, without network alarm monitoring functions you may not need.
The NetGuardian 832A controls local access at your remote sites. This unit maintains a list of personnel who are authorized to access the facility. It records all valid entries, attempts, and the time of each action in non-volatile RAM. It can also receive control from T/Mon to remotely open a door.

The NetGuardian indicates conditions such as valid entry, invalid access attempt, and system lockout. The unit supports up to 1,300 user profiles for distribution between door entry points.
The Entry Control Unit, or simply ECU, acts as an interface between the NetGuardian and the proxy reader. Any access code that's entered is accepted by the ECU and passed on to the NetGuardian for validation.

A proximity card reader eliminates the chance of forgotten keycodes and increases your level of access control. An employee can easily share a keycode with others, but not a proxy card.
In the event that a card is lost or stolen, it can be deactivated in seconds and a new card may be issued in its place.

You may not care about door alarm arming and disarming during business hours, but a door that's propped for more than 3 minutes is a potential threat that you must know about.
So, if your main concern is a door propped alarm or door propped open alarm, you can set your BAS' Derived Alarm timer at about 30 seconds to throw alarms after "Door Open" has been standing for 30 seconds straight, for example.

There are some cases, however, when you may want to allow a door to be held open or to remain unlocked. The BAS propped door features allow you to accommodate special access needs at your sites, such as door open times and schedules for doors to stay closed.
We've put together the How to Deploy an advanced Building Access System White Paper to answer any other questions about remote site access and remote monitoring.
Get your free copy of the White Paper today to know more about how you can protect your revenue through site monitoring.

Morgana Siggins
Morgana Siggins is a marketing writer, content creator, and documentation specialist at DPS Telecom. She has created over 200 blog articles and videos sharing her years of experience in the remote monitoring industry.