Check out our White Paper Series!
A complete library of helpful advice and survival guides for every aspect of system monitoring and control.
1-800-693-0351
Have a specific question? Ask our team of expert engineers and get a specific answer!
Sign up for the next DPS Factory Training!

Whether you're new to our equipment or you've used it for years, DPS factory training is the best way to get more from your monitoring.
Reserve Your Seat TodayIf your network is spread out across a wide area with many unmanned sites, you need an SNMP monitoring system. It's virtually impossible for you and your team to watch all of your gear without some form of automated monitoring.
SNMP monitoring is distinct from other forms of monitoring because it uses the Simple Network Management Protocol (SNMP). SNMP messages are, most commonly, created by an SNMP agent (some kind of gear at your site). And they are received by a central SNMP manager (a software program, ideally running on its own dedicated hardware platform).
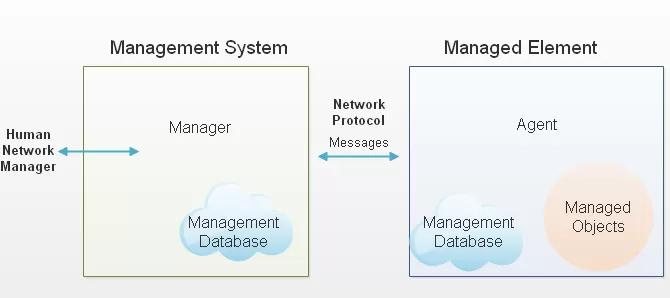
This protocol is one of the most popular in the remote monitoring word today because it can bring you many benefits. And there really aren't any significant disadvantages to be wary of.
Of course, using this popular protocol isn't without some threats. Anytime you use something that is common, there will be a larger population of people who are familiar with it.
Some of these people may have ill intent. They might use the common knowledge of SNMP to break into your system. There are strong cyber terrorism issues here.
For many years, the lack of security in SNMP was viewed by many as its Achilles' heel. For all its wonderful business benefits, the threat of cyber terrorists and virtual vandals loomed large.
However, SNMP monitoring is no longer without any defenses. SNMP community string is a common security feature in SNMP devices. And there are also some other SNMP security best practices that you should know about.
SNMP community string is an SNMP security password that devices need to talk to each other. It's similar to a user ID or password that allows you to access your equipment's data.
Your SNMP monitoring device should send the community string along with SNMP requests. If the community string is correct, then your device will answer with the requested information. However, if the community string is incorrect, your device will simply disregard the request and will not respond.
SNMP community strings are specifically used within SNMPv1 and SNMPv2c protocols. These strings act as a simple password system to control access to devices on a network. In contrast, SNMPv3 utilizes a more advanced authentication process involving a username/password and an encryption key.
Many SNMPv1 and SNMPv2c devices are initially configured with a default "public" read-only community string. It's crucial for network administrators to customize these settings to enhance security, as leaving them unchanged can pose significant risks.
SNMP community strings are case-sensitive. This means that "CommunityString" and "communitystring" would be considered entirely different strings. An SNMP community string generally ranges from 1 to 32 characters in length. When it comes to their composition, these strings can include any combination of letters (both uppercase and lowercase), numbers, and symbols. Being mindful of the case sensitivity and complexity of these strings is crucial for maintaining secure and accurate network monitoring.
It's important to protect and take care of community strings because they serve as keys to accessing and managing your network devices. If compromised, attackers can gain unauthorized control, leading to potential security breaches, data loss, or network downtime. The best practices for creating SNMP community strings involve:
By following these practices, you can strengthen your SNMP security and protect your network from unauthorized access.
There are three different kinds of community string:
Although the community string does offer some security, it's only used by devices that support the versions SNMPv1 and SNMPv2.
SNMPv1 was the first version of SNMP. It uses community strings to restrict access. This version uses read-write and read-only community strings, but the data transmitted is unencrypted. Which means it can be easily attacked and exploited.
SNMPv2c delivers data encryption, but it uses data types, like 64-bit counters - not present in SNMPv1. This means that this sub-version of SNMPv2 is a little bit more secure than SNMPv1. It uses two types of community string: read-only and read-write.
The read-only community string allows access to management information base (MIB) objects on a read-only basis. MIB objects are the data exchanged between an SNMP agent and the SNMP manager.
The read-write community string will allow you to access and interact with these MIB objects. This means that you can edit settings of your devices by logging into the manager.
Other advantages of SNMPv2c include:
Not all devices are SNMPv2c compliant, so your SNMP manager should be downward compatible with SNMPv1 devices. You can also use SNMPv3 mediation devices to ensure compatibility.
Another point to remember is that SNMPv1 and v2c equipment have their SNMP default community string set to "public." So, you'll have to change all of your community strings to customized values during the device setup.
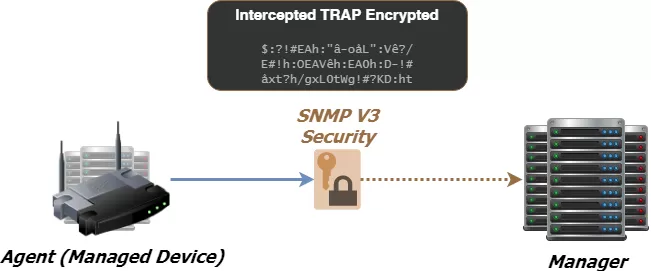
Now, SNMPv3 is the newest version of the SNMP protocol. Its primary feature is enhanced security. It allows you to fully encrypt messages, so they can't be accessed or intercepted by unintended people.
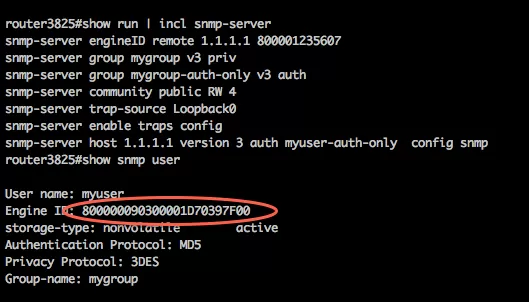
The "EngineID" Identifier in SNMPv3 uniquely identifies each SNMP entity. Conflicts can occur if two SNMP entities have duplicate EngineIDs. The EngineID is used to generate the key for authenticated messages.
SNMPv3 security comes primary in two forms:
SNMP community strings do offer you some security, but the best practice is to have encrypted SNMPv3.
To confirm that an SNMP community string is working, you can use an SNMP management tool or command-line utility to send a request to a device using the community string. If the string is correct and the device is configured properly, the device will respond with the requested information, such as system details or performance metrics. Common tools like SNMPWALK or SNMPGET can be used to query the device. If the string is incorrect, the device will either not respond or return an error message, indicating a failed authentication.
To ensure your network operates securely, it's crucial to manage SNMP credentials effectively. SNMP credentials are the keys that enable network managers to monitor and control devices. Knowing how to locate and configure these SNMP credentials is vital for maintaining the integrity and security of your network.
To find SNMP credentials, access the device's management interface via a web browser, SSH, or Telnet. Login with the admin username and password. Then, navigate to the SNMP settings section. this section is usually labeled "SNMP" or "Network Management." For SNMPv1/v2c, look for community strings. For SNMPv3, find user accounts along with their authentication and privacy settings.
For DPS Telecom devices like the NetGuardian series and T/Mon, access the web interface using the device's IP address. After logging in, navigate to the SNMP configuration section to view or configure community strings for SNMPv1/v2c or user credentials for SNMPv3. Always follow your organization's security policies, using secure passwords and enabling encryption options provided by SNMPv3.
Configuring SNMP (Simple Network Management Protocol) community strings is a necessary step in managing network devices. Here's a step-by-step guide to configuring them on both Windows and Linux systems.
1. Access SNMP Service Properties:
Navigate to the SNMP Service Properties window relevant to your operating system version.
2. Add a New Community String:
Go to the Security tab and click on the Add button.
Enter your desired community string.
Choose appropriate access rights, typically READ ONLY or READ WRITE, based on your network security needs.
1. Edit the Configuration File:
Open the /etc/snmp/snmpd.conf file with your preferred text editor.
2. Create a Community String:
For a read-only string, add a line like: rocommunity public.
For read-write access, use: rwcommunity private.
3. Additional Step for Ubuntu:
Modify /etc/default/snmpd file. Change the line:SNMPSDOPTS=' -lsd -Lf dev/null -u snmp -p /var/run/snmpd.pid' to :SNMPDOPTS=' -Lsd -Lf /dev/null -u snmp -I -smux -p /var/run/snmpd/pid -c /etc/snmp/snmpd/conf'
4. Restart and Enable SNMP Service:
Save and close your configuration files.
Restart the SNMP daemon and enable the service with:/etc/init.d/snmpd restart sysv-rc-conf snmpd on
Pro Tips:
While editing the snmpd.conf file, look for comments (lines starting with #). These lines often contain useful examples and additional information. By carefully following the steps above, you can efficiently set up SNMP community strings, ensuring secure management of network devices.
SNMPv3 support is a standard feature of the NetGuardian 832A G5 RTU. This allows you to monitor all of your SNMP devices with enhanced security via message encryption. The NetGuardian allows you to report alarms in SNMP v1, v2c, or v3. This leverages the full NetGuardian feature set and your existing SNMP management station.
The NetGuardian 832A G5 provisioning tools allow you to set up advanced SNMPv3 applications. For example, you can choose which SNMP versions managers may use to communicate with your NetGuardian. By restricting your managers to v3 only, you're requiring them to use that protocol's enhanced security. In environments where security is less of a concern, you can allow all SNMP versions to maximize flexibility.
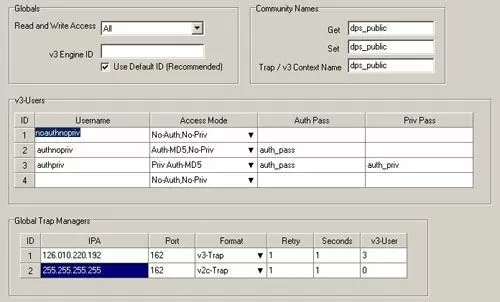
This RTU also automatically generates a unique EngineID to eliminate conflicts caused by duplicate IDs. You can modify your NetGuardian's default v3 EngineID for advanced SNMP applications, but this is recommended only for experienced users.
Using SNMPv3, the NetGuardian 832A encrypts its messages with CBC-DES encryption, a part of the Universal Security Model (USM). The encrypted data appears scrambled if it is intercepted, rendering it unreadable by anyone but the intended recipient. This makes SNMPv3 your best option when routing SNMP messages over the Internet.
This is ideal for companies with mission-critical infrastructure requiring high security. Even on a secured network, SNMPv3 encryption will provide an additional layer of redundant security.
Also, the 832A supports unique security profiles for up to four users. Each user can be assigned a unique set of security parameters, including authentication and/or privileged access to SNMP.
To learn more fundamental SNMP protocol concepts, just download your free copy of The Fast Track Introduction to SNMP.
This white paper is a quick and easy (but solid and foundational) introduction to SNMP. It has been created to give you the information you need to successfully implement SNMP-based alarm monitoring in your network. It's an introduction to SNMP from the perspective of telecom network alarm management.
Summarizing the history and structure of the protocol you'll see some concrete applications for using SNMP in internal network alarm environments. You'll also see diagrams and read plain-English descriptions that teach you the basics in an intuitive way.
And don't hesitate to call one of our SNMP experts to ask a specific question, though. We can offer basic guidance as you learn SNMP, even if you don't need to purchase any new equipment.

Andrew Erickson
Andrew Erickson is an Application Engineer at DPS Telecom, a manufacturer of semi-custom remote alarm monitoring systems based in Fresno, California. Andrew brings more than 19 years of experience building site monitoring solutions, developing intuitive user interfaces and documentation, and opt...